The Problem.
There is a misconception that credential breaches are done by hackers and a delusion that your own mailbox is just not that enticing. It is not hackers going after you, it is scammers attempting to make a quick profit. Scamming is all about simple economics because each hijacked account presents two opportunities. The first opportunity is a direct attempt at committing fraud, and the second is the opportunity to create more opportunities. The payouts on both can be a few dollars or many thousands of dollars and they continue to pay dividends over time. It is also extremely easy and much less work that driving for Uber or doing grocery delivery.
Your e-mail credentials are also the lowest hanging fruit in the scam world because your relevant information had already been breached. Before a scammer gets their hands on this fruit, hackers exploit major companies and complete difficult jobs with high payouts. Take, for example, the DoorDash breach announced this week of 4.9 million users:
Approximately 4.9 million consumers, Dashers, and merchants who joined our platform on or before April 5, 2018, are affected… Profile information including names, email addresses, delivery addresses, order history, phone numbers, as well as hashed, salted passwords — a form of rendering the actual password indecipherable to third parties.
While there are only a few hackers successful at major breaches, there is a nearly unlimited supply of scammers willing to go after the scraps. While DoorDash did not breach plain-text passwords, such compromises are common. Pretend that passwords were exposed and 4.9 million passwords were suddenly available on the ominous sounding DarkWeb. Initially that list would sell for thousands of dollars, but with time the price would eventually reach nothing. Even so, the information within would still have value to scammers.
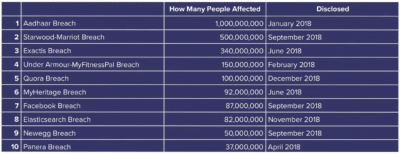
Although you may not have used DoorDash, there is a good chance that one of the companies breached in the last few years did disclose your data. That list is massive and includes Starwood-Marriott, FaceBook, Panera, Adapt, Adobe, Apollo, CafePress, MySpace, Verifications.IO, Online Spambot, Bitly, DropBox, Canva, Hautelook, Houzz, LinkedIn, MyHeritage, Poshmark, ShareThis, Trillian, Wanelo, Zomato, WhitePages, and the list goes on.
There’s more! In February 2018, a massive collection of almost 3,000 alleged data breaches was found online. Whilst some of the data had previously been seen in, 2,844 of the files consisting of more than 80 million unique email addresses had not previously been seen. Each file contained both an email address and plain text password.
Scammers will take the available information from a disclosed list and try it against other services. For the sake of argument, pretend that you did use DoorDash. They would take that information and using manual labor as well as elementary bots/scripts being testing other systems such as Outlook and G-Mail. If you happen to be a humanoid that re-used a password, like nearly everyone in your shouting distance, there is a good chance that a scammer will figure this out. Despite there being billions of account possibilities, cloud computing makes all of these attempts cheap and easy. Should your mailbox be one of those things that is protected by a compromised password, odds are someone has already figured it out and you are already a victim.
Should scammers access your mailbox they will begin to review all of your communication, target easy frauds such as bank accounts, reset passwords to valuable services, redirect mail, and spread the malice to your contacts. In some cases this can be catastrophic and can remain undetected for days, weeks, or months. For the full story on how this kind of scam evolves, visit us on Medium.com. Surely, you can imagine what may happen.
The Solution
A small, but important, part of mitigating credential compromise in a business is a password manager. We choose to use 1Password Teams and so do many of our customers. Confronted with more frequent breached accounts we reached out to AgileBits, the developers of 1Password Teams, and asked them for an incentive. In turn, they gave us $2000 in service credits which we can distribute in $100 parcels to the first 20 customers that contact us. We added a one-hour implementation session at no-cost. While a single hour is a not enough to fully implement 1Password Teams, it is enough to get the account provisioned and get the ball rolling.
1Password Teams is not a silver-bullet. It takes patience, commitment from owners and staff, and time. However, we believe that companies that adopt 1Password Teams are substantially better off. 1Password Teams provides insight into your credential management through reports and analysis, notifies you or problems, and enables you to store randomly generated and unique passwords for every website and web app you use. Combined with multi-factor authentication for Outlook, G-Suite, Remote Desktop, and File Sharing companies begin to close massive holes in their security. We believe that you can rely on 1Password Teams to protect your data, fortify your defenses, and empower your employees to make better security decisions.
The choice should be easy. You can begin a 30-day trial for 1Password Teams directly through their website. Also, reach out to us via our web form and let us know that you did, and we will share with you one of our $100 credits and schedule the one-hour session.
TechBento receives no commission, bonuses, incentives or payments for this referral. This is us working as fiduciaries for our clients. Faced with a common problem among many of our customers, we negotiated discounts with a vendor and developed an implementation plan that includes us committing resources to your business.

