The Apple macOS security and privacy features make remote management tough. Apple’s macOS Sierra introduced new security features that simplify apps from the App Store, but complicate everything else. This spells trouble for applications that need a lot of access, such as antivirus. The reason they are complicated is quite simple: these applications expect lots of access to do their jobs. Meanwhile, macOS does everything possible to limit their power in an effort to keep users safe. The bridge to allowing this is the Kernel Extension Policy Control which allows remote administrators – through systems such as Mobile Device Management (MDM) – to grant permission to an application and deploy it. Here is how this works in practice:
Collect KEXT info…
First, I collect the “Bundle ID” and “Team ID” for WebRoot. Although I can open the plist or check the signature my favorite option is the community assembled spreadsheet. Why is this necessary? Apple’s macOS checks the authenticity of each application by verifying a digital signature.
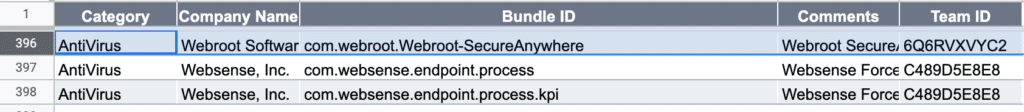
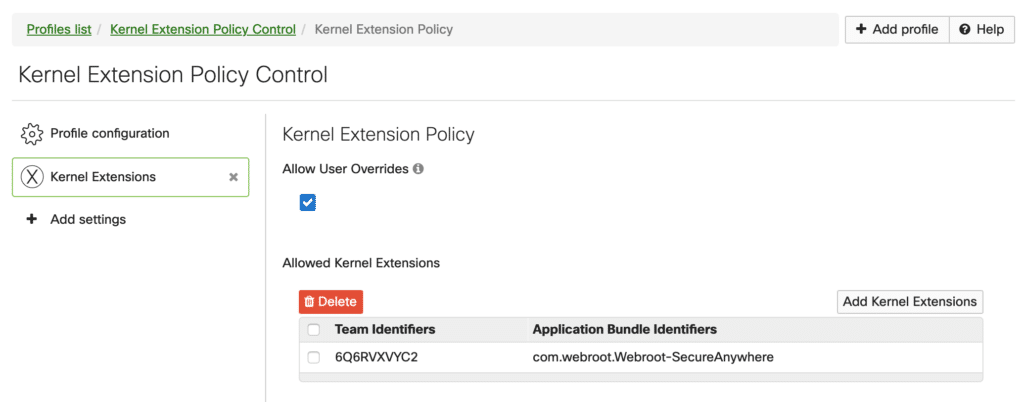
Distribute Kernel Policy Extension Control…
Once I have values, I build and ship the Kernel Extension Policy Control using my Mobile Device Management solution. Knowing that MDM KEXT features are relatively new, this is a good time to add exceptions for common used tools like TeamViewer, ScreenConnect, etc.
Automate WebRoot silent installation using BASH…
Now, for the automation portion. I use Ansible and SaltStack to run automation on macOS devices, so this is easy. All I do is write a short BASH script to download and install Webroot. However, there is a small setback. My deployments have already been using WebRoot and my goal is not just to install on new systems, I want to fix all the old systems that are not reporting. My script is designed to blow out the entire config and start fresh using a silent install. Actually, it might be more complicated than that! My users are not local administrators, so I am not entirely sure if their WebRoot is running as them or as sudo. I want to cover all of my bases, thus my script tries a few things in an effort to remove the old and install the new.
#!/bin/bash
launchctl unload /Library/LaunchDaemons/com.webroot.security.mac.plist
launchctl unload /Library/LaunchDaemons/com.webroot.webfilter.mac.plist
sudo launchctl unload /Library/LaunchDaemons/com.webroot.security.mac.plist
sudo launchctl unload /Library/LaunchDaemons/com.webroot.webfilter.mac.plist
rm /usr/local/bin/WSDaemon
rm /usr/local/bin/WFDaemon
sudo rm /usr/local/bin/WSDaemon
sudo rm /usr/local/bin/WFDaemon
killall -9 WSDaemon
killall -9 WFDaemon
killall -9 "Webroot SecureAnywhere"
sudo killall -9 WSDaemon
sudo killall -9 WFDaemon
sudo killall -9 "Webroot SecureAnywhere"
rm -rf /System/Library/Extensions/SecureAnywhere.kext
rm -rf "/Applications/Webroot SecureAnywhere.app"
rm /Library/LaunchAgents/com.webroot.webfilter.mac.plist
rm /Library/LaunchDaemons/com.webroot.security.mac.plist
sudo rm -rf /System/Library/Extensions/SecureAnywhere.kext
sudo rm -rf "/Applications/Webroot SecureAnywhere.app"
sudo rm /Library/LaunchAgents/com.webroot.webfilter.mac.plist
sudo rm /Library/LaunchDaemons/com.webroot.security.mac.plist
sudo rm -rf "/Applications/Webroot SecureAnywhere.app"
curl -o /tmp/wsamacsme.dmg http://anywhere.webrootcloudav.com/zerol/wsamacsme.dmg
hdiutil attach -nobrowse /tmp/wsamacsme.dmg
cp -R "/Volumes/Webroot SecureAnywhere/Webroot SecureAnywhere.app" /Applications/
diskutil unmount "/Volumes/Webroot SecureAnywhere"
sudo "/Applications/Webroot SecureAnywhere.app/Contents/MacOS/Webroot SecureAnywhere" install -keycode="1111-WRSM-1111-1111-1111" -language=en -silent

